HIPAA Security Standards Compliance Assessment
Background
Health information means any information, including genetic information, whether oral or recorded in any form or medium, that:
- Is created or received by a health care provider, health plan, public health authority, employer, life insurer, school or university, or health care clearinghouse; and
- Relates to the past, present, or future physical or mental health or condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual.
- Transmitted by electronic media;
- Maintained in electronic media; or
- Transmitted or maintained in any other form or medium.
Together, HIPAA and HITECH Act rules include:
- The Privacy Rule, which requires appropriate safeguards to protect the privacy of PHI and imposes restrictions on the use and disclosure of PHI without patient authorization. It also gives patients the rights over their health information, including rights to examine their health records and request corrections.
- The Security Rule, which sets the standards for administrative, technical, and physical safeguards to ensure the confidentiality, integrity, and security of electronic PHI.
- The Breach Notification Rule, which requires covered entities and their business associates to provide notification when a breach of unsecured PHI occurs.
Viedoc is a software platform developed to facilitate clinical research involving natural persons having given their informed consent to participate in clinical trials. The HIPAA Privacy Rule establishes the conditions under which protected health information may be used or disclosed by covered entities for research purposes. Research is defined in the Privacy Rule (45 CFR 164.501) as:
Viedoc Technologies have no insight in the data customers process on the Viedoc platform but have implemented measures that enable customers to stay compliant with these regulations. This document describes how customer information is processed on the Viedoc platform, the organizational and technical measures implemented to protect information security, and the implementation status of the security standards defined in 45 CFR 164 subpart C (“Security Standards for the Protection of Electronic Protected Health Information”). While Viedoc Technologies is generally not subject to the Security Standards for the Protection of Electronic Protected Health Information through its provision of services, Viedoc Technologies has evaluated the Viedoc platform using this set of standards, as this is the most comprehensive data security rule in the United States.
Description and purpose of data processing
Health information
Viedoc Technologies is a “blind” processor of customer research data. Thus, the specifics of the health information processed, and whether this is classified as protected health information, is not known to Viedoc Technologies.
The purpose of the information processing on the Viedoc platform is to conduct scientific studies involving clinical research, and the necessity and proportionality is a responsibility of the study sponsor (in most cases the same as the customer of Viedoc Technologies). The data collection is outlined by a study protocol that typically undergoes review and approval by ethical committees and competent regulatory authorities.
The data collection is typically initiated with the following actors and sequence of events:
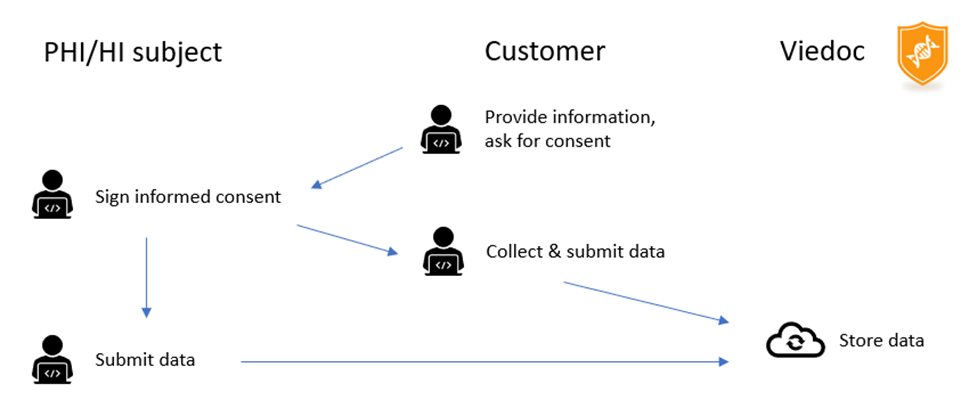
Data Flow
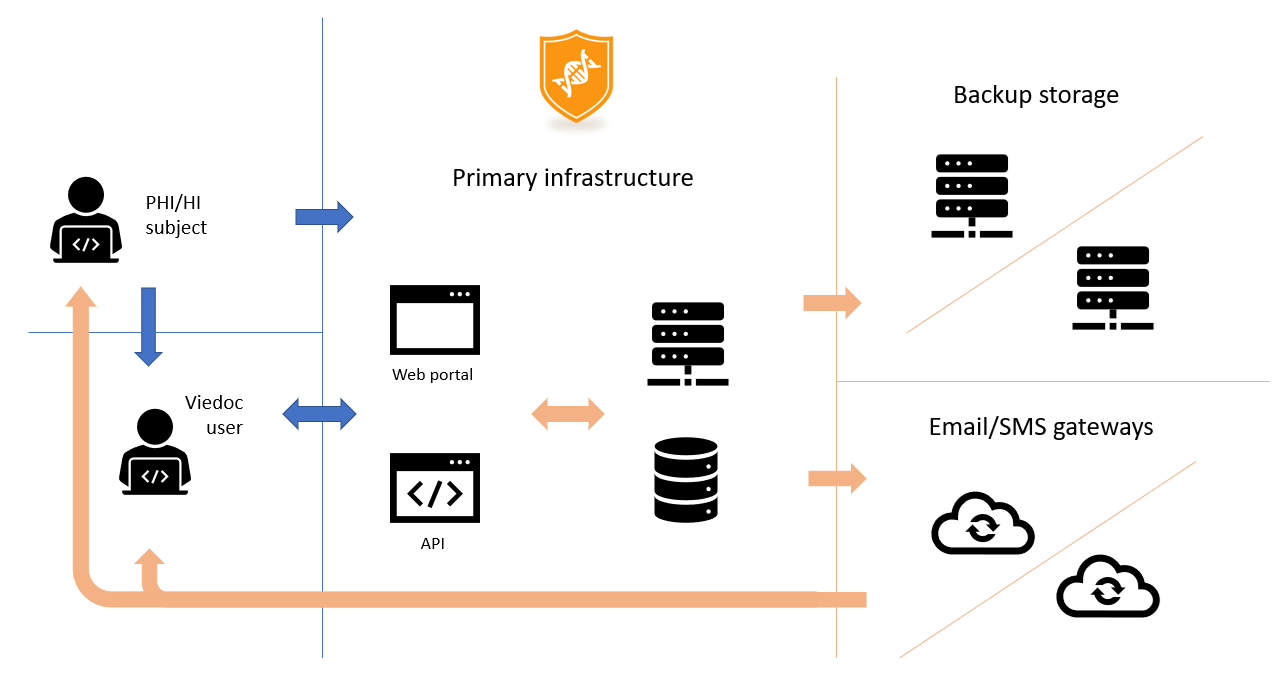
Data locality and sub-processors
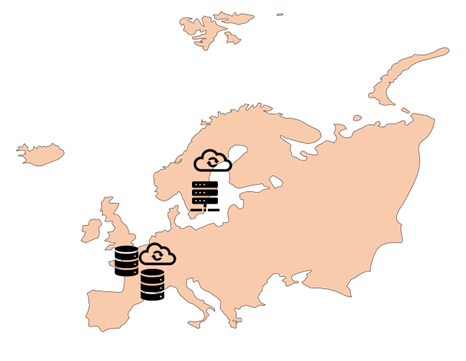
European instances
The primary infrastructure of the European instance of Viedoc is located in France with U.S. sub-processor Microsoft and their Azure platform. Backup storage and email/SMS gateways are also located in Europe with sub-processors MailJet, Elastic Email and SMS-Teknik.
Japanese instances
The primary infrastructure of the Japan instance of Viedoc is located in Japan with U.S. sub-processor Microsoft and their Azure platform. Backup storage and email/SMS gateways are located in Japan and Europe with sub-processors HENNGE, Elastic Mail, and SMS-Teknik.
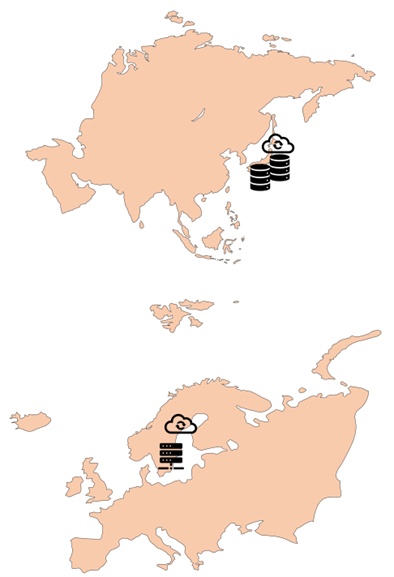

Chinese instances
The primary infrastructure of the China instance of Viedoc is located in mainland China with sub-processor 21ViaNet and their national instance of the Microsoft Azure platform. Backup storage and email/SMS gateways are also located in China with sub-processors AliYun and AWS China.
The US instances
The primary infrastructure of the US instance of Viedoc is located in US with sub-processor Microsoft and their Azure platform. Backup storage is also located in US with sub-processor AWS. Email/SMS gateways are located in Europe with sub-processors MailJet, Elastic Email and SMS-Teknik.

Risk and risk mitigation
Processing context
Viedoc is a data collection platform for clinical research and is not designed to be used as a medical device or clinical decision support system for treatment of study subjects. This is stated in the General Terms and Conditions (GTC) that all customers enter into, as well as in the Terms of Use that all platform users enter into.
In addition, the GTC also state that whenever the Viedoc alert functionality is utilized for safety procedures, e.g. as a means for serious adverse event awareness, this functionality cannot be solely relied on. There must be additional safety procedures implemented.
These statements serve to avoid risks that inappropriate platform usage could result in. If used according to the platform terms, erroneous data in, or unavailability of, Viedoc, should not pose a direct physical risk to the natural persons whose information is processed on the platform.
Privacy by design and risk avoidance
The Viedoc platform, the Viedoc service offering and the Viedoc Technologies organization is designed with privacy and information security in mind. Some of the measures to ensure privacy by design and to avoid the worst risks include:
- Structured processing of all data, detailed data inventory and mapping of data processing
- GTC statement that it is a customer responsibility and requirement to pseudonymize data before input 1)
- Organizational and technical access controls that prevent Viedoc Technologies employees from accessing customer data
1) It is however possible to override this in the Data Processing Agreement appendix.
Baseline risk minimization and mitigation measures
Viedoc Technologies have implemented a risk-based Information Security Management System (ISMS) that is certified according to ISO 27001 and facilitates a structured and continuous approach to information security. All ISO 27001 annex A controls are included in our scope of applicability, some of which are:
- Continuous information security awareness training of all staff
- Separation of duties
- Separation of development and production environments
- Use of the principle of least privilege
- Network segmentation, firewalls
- Continuously updated anti-malware
- Management of technical vulnerabilities
- Security testing built into development lifecycle
- Continuous vulnerability scans
- Recurring third party penetration tests
- End to end encryption in transit both externally as well as internally
- Encryption at rest
- Audits of, and data protection agreements with, our sub-processors
HIPAA security standards
The following table lists the Viedoc Technologies implementation status of the safeguards outlined by Subpart C of 45 CFR 164.
|
Standards |
Subsection of §164 |
Implementation Specifications |
Status |
|
Administrative Safeguards |
|
||
|
Security Management Process |
308(a)(1) |
Risk Analysis (R) |
Implemented |
|
Risk Management (R) |
Implemented |
||
|
Sanction Policy (R) |
Implemented |
||
|
Information System Activity Review (R) |
Implemented |
||
|
Assigned Security Responsibility |
308(a)(2) |
(R) |
Implemented |
|
Workforce Security |
308(a)(3) |
Authorization and/or Supervision (A) |
Implemented |
|
Workforce Clearance Procedure |
Implemented |
||
|
Termination Procedures (A) |
Implemented |
||
|
Information Access Management |
308(a)(4) |
Isolating Health care Clearinghouse Function (R) |
N/A |
|
Access Authorization (A) |
Implemented |
||
|
Access Establishment and Modification (A) |
Implemented |
||
|
Security Awareness and Training |
308(a)(5) |
Security Reminders (A) |
Implemented |
|
Protection from Malicious Software (A) |
Implemented |
||
|
Log-in Monitoring (A) |
Implemented |
||
|
Password Management (A) |
Implemented |
||
|
Security Incident Procedures |
308(a)(6) |
Response and Reporting (R) |
Implemented |
|
Contingency Plan |
308(a)(7) |
Data Backup Plan (R) |
Implemented |
|
Disaster Recovery Plan (R) |
Implemented |
||
|
Emergency Mode Operation Plan (R) |
Implemented |
||
|
Testing and Revision Procedure (A) |
Implemented |
||
|
Applications and Data Criticality Analysis (A) |
Implemented |
||
|
Evaluation |
308(a)(8) |
(R) |
Implemented |
|
Business Associate Contracts and Other Arrangement |
308(b)(1) |
Written Contract or Other Arrangement (R) |
Implemented 2) |
|
Physical Safeguards |
|
||
|
Facility Access Controls |
310(a)(1) |
Contingency Operations (A) |
Implemented |
|
Facility Security Plan (A) |
Implemented |
||
|
Access Control and Validation Procedures (A) |
Implemented |
||
|
Maintenance Records (A) |
Implemented |
||
|
Workstation Use |
310(b) |
(R) |
Implemented |
|
Workstation Security |
310(c) |
(R) |
Implemented |
|
Device and Media Controls |
310(d)(1) |
Disposal (R) |
Implemented |
|
Media Re-use (R) |
Implemented |
||
|
Accountability (A) |
Implemented |
||
|
Data Backup and Storage (A) |
Implemented |
||
|
Technical Safeguards |
|
||
|
Access Control |
312(a)(1) |
Unique User Identification (R) |
Implemented |
|
Emergency Access Procedure (R) |
Implemented |
||
|
Automatic Logoff (A) |
Implemented |
||
|
Encryption and Decryption (A) |
Implemented |
||
|
Audit Controls |
312(b) |
(R) |
Implemented |
|
Integrity |
312(c)(1) |
Mechanism to Authenticate Electronic Protected Health Information (A) |
Implemented |
|
Person or Entity Authentication |
312(d) |
(R) |
Implemented |
|
Transmission Security |
312(e)(1) |
Integrity Controls (A) |
Implemented |
|
Encryption (A) |
Implemented |
||
2) Viedoc European and Japan instances
Continuous risk management
Risk management is continuous work. The context Viedoc Technologies operate in is constantly changing and we have implemented procedures to continuously identify and treat new risks.
Viedoc Technologies have performed a specific HIPAA risk assessment using the Security Risk Assessment Tool provided by HealthIT.gov / Office of the National Coordinator for Health Information Technology (ONC) / Office of the Secretary for the U.S. Department of Health and Human Services (HHS). If the customer chooses to use either the European, Japanese or US instance of Viedoc, for which Viedoc Technologies have HIPAA business associate agreements in place with Microsoft as part of the Service Terms, the reported Risk Score was 3%.
