Activating SSO
Introduction
This use case shows how users can authenticate themselves in Viedoc using an external identity provider (IdP) instead of the built-in identity provider, and thus being able to log in using single sign-on (SSO).
The users identify themselves with an email address containing a domain name—below referred to as hostmaster@your.domain.name—that the user owns or that you as the Organization Administrator is in control of.
Note! For more information about using SSO for Viedoc, see the lesson Single sign-on.
We go from this:
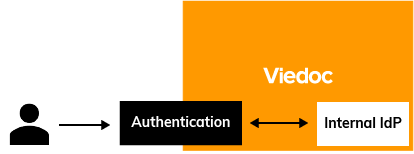
...to this:

Using Google Workspace as IdP
Pre-requisites
-
The domain name for which you want to configure SSO must have an email address like this: hostmaster@your.domain.name, and you must be able to get hold of a key sent to that address.
-
You must have Organization Administrator access to Viedoc.
-
You must have Administrator access to Google Workspace.
Step-by-step guide
In this guide we use the domain name fubar.se and the European Viedoc training instance.
| 1 |
As Organization Administrator, go to Admin and select Organization Settings: 
|
| 2 |
Select SSO > Add SSO configuration, enter the Domain name and select Continue. 
|
| 3 |
Contact the person in your organization with access to the hostmaster@your.domain.name email inbox, to retrieve the verification key that proves that you own the domain. 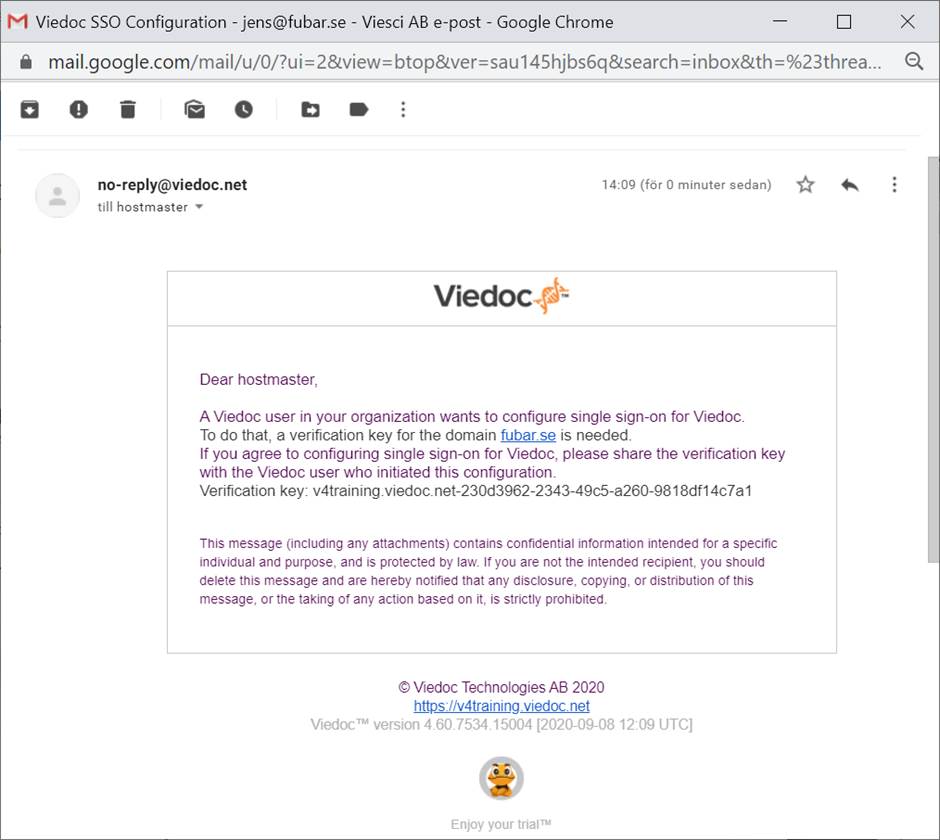
|
| 4 |
Enter the verification key in Viedoc and select Verify. 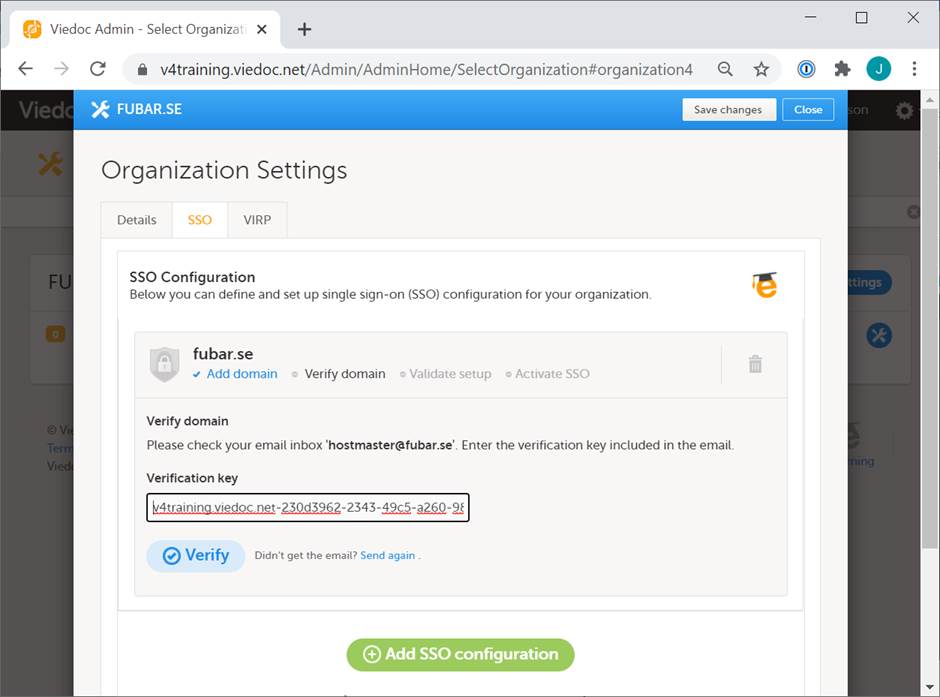
|
| 5 |
Make a note of the Redirect URL and the Entity ID. 
|
| 6 |
In a separate tab, log in to Google Workspace Admin Console, go to Apps > SAML apps. 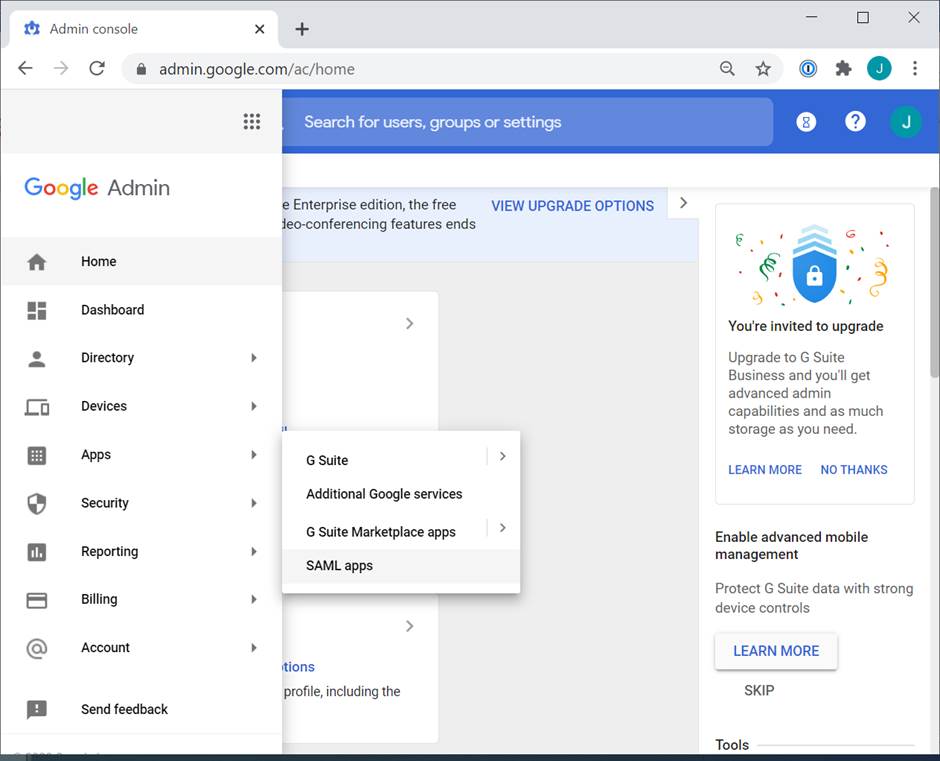
|
| 7 |
Select Add service and SETUP MY OWN CUSTOM APP: 
|
| 8 |
From the Google IdP Information window:
Select Save. 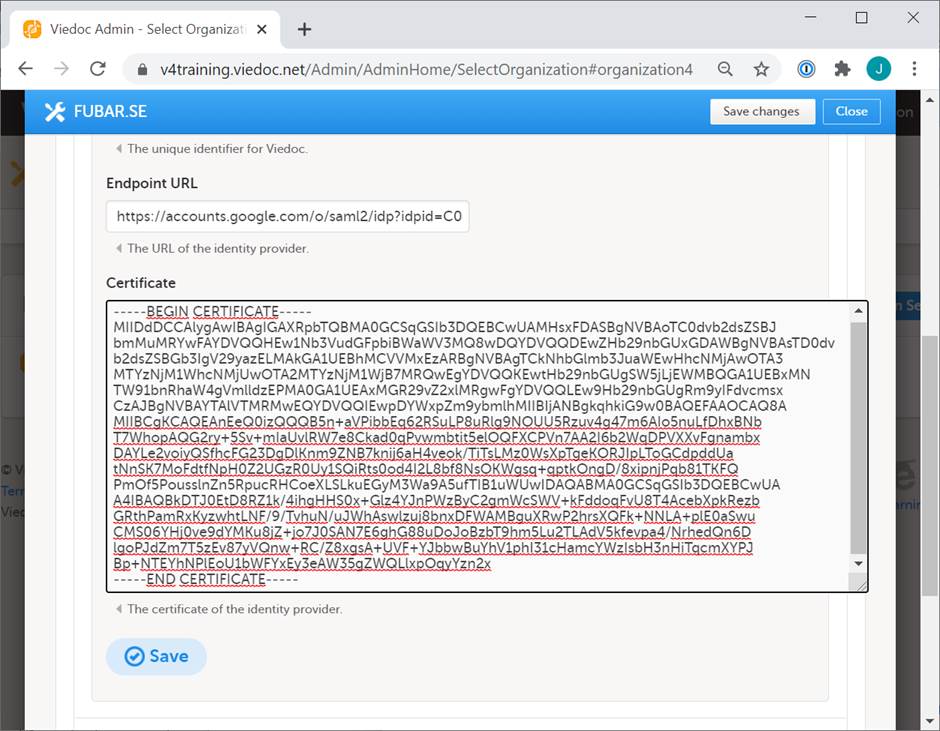
|
| 9 |
In Viedoc, copy the redirect URL and go back to the Google Workspace tab and select Next. |
| 10 |
In the Basic information for your Custom App window:
Select Next. 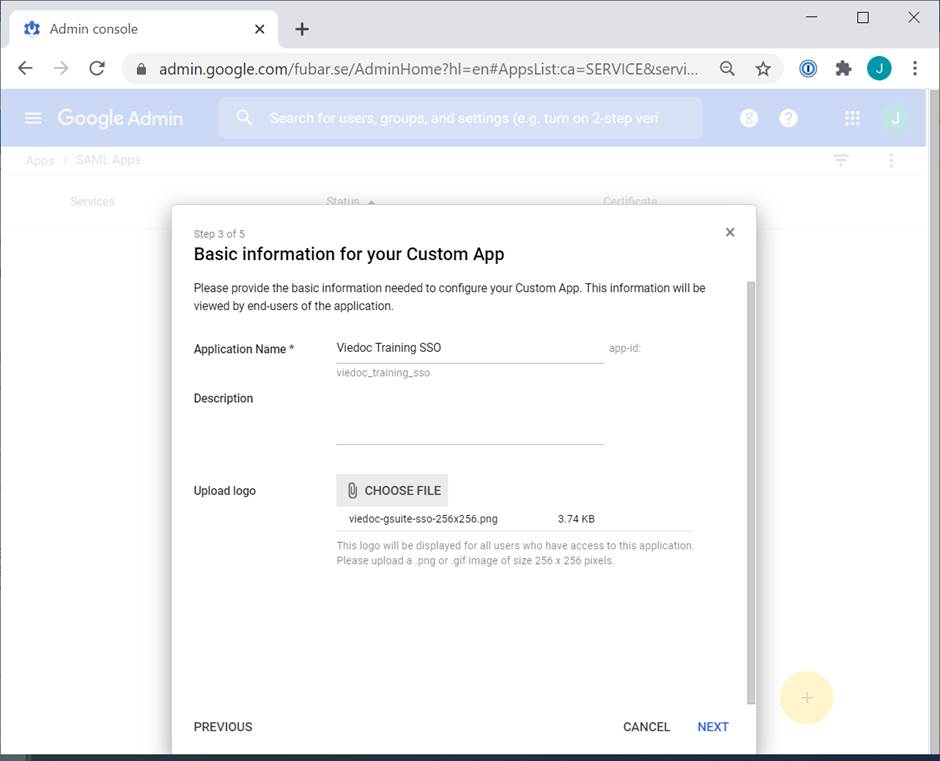 |
| 11 |
In the Service Provider Details window:
Select Next. 
|
| 12 |
In the Attribute Mapping window, select Finish. 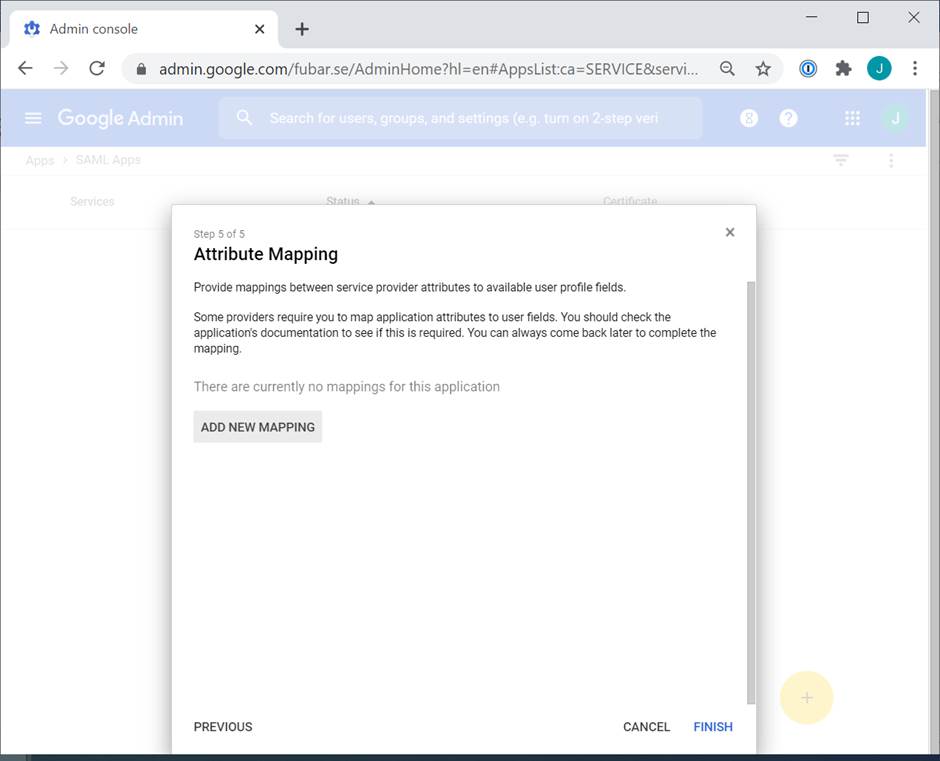
|
| 13 |
Select OK. 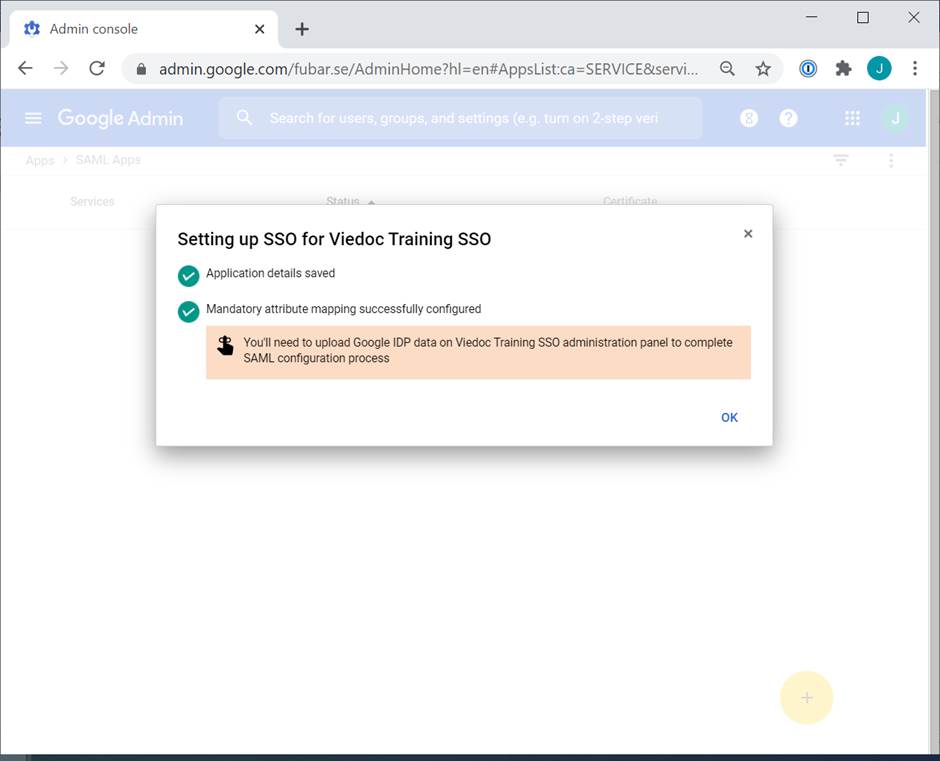
|
| 14 |
Select the down arrow of the User access section of the newly configured SAML App. Select ON for everyone and Save. 
|
| 15 |
Go back to the Viedoc tab and select Validate. Note! You might be prompted to enter your email address and password in order to authenticate with your IdP if not already logged in. Upon successful authentication you will automatically be redirected to the domain verification page. 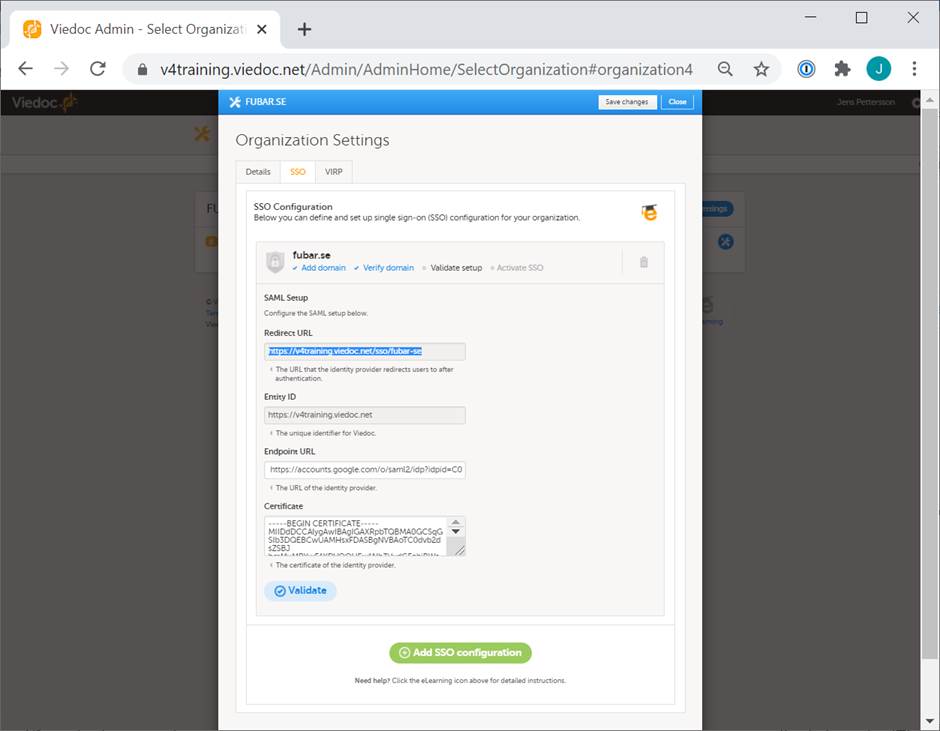
|
| 16 |
Verify that the domain is validated and then close the tab. 
|
| 17 |
Select Next. 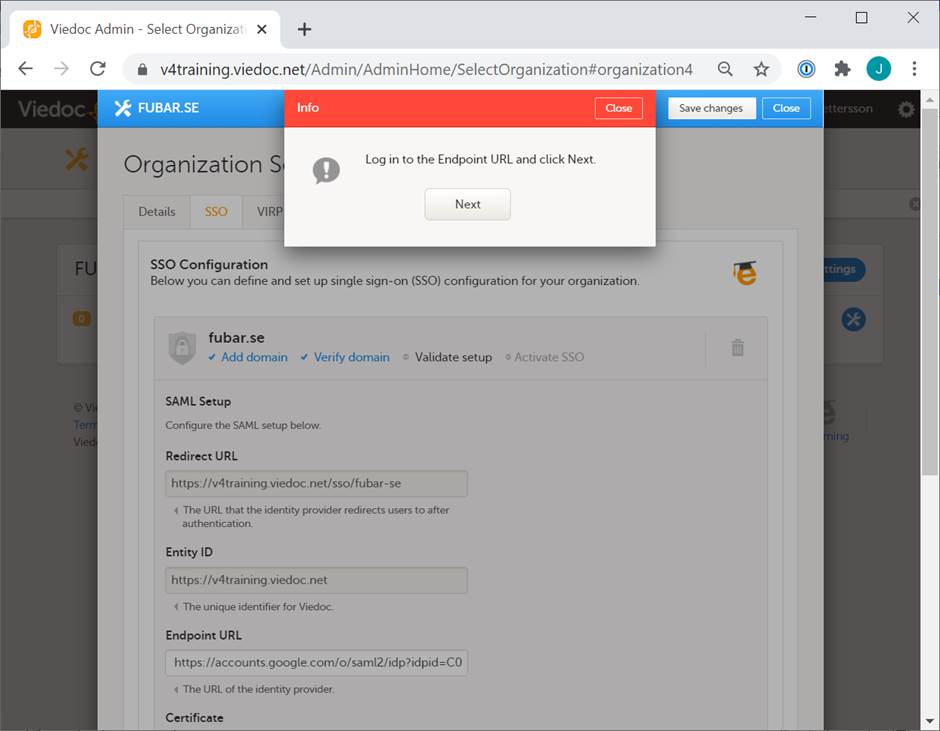
|
| 18 |
The SSO configuration is now completed. When all users are informed about the new login URL—with the configured domain as their login name (the primary email address is used for authentication in both the IdP and in Viedoc)—select Activate > Yes. 
|
Using Microsoft Azure AD as IdP
Pre-requisites:
-
The domain name for which you want to configure SSO must have an email address like this: hostmaster@your.domain.name, and you must be able to get hold of a key sent to that address.
-
You must have Organization Administrator access to Viedoc.
-
You must have Administrator access, or higher, in Microsoft Azure Active Directory (AD).
Step-by-step guide
In this guide we use the domain name pcg-solutions.com and the European Viedoc training instance.
| 1 |
As Organization Administrator, go to Admin and select Organization Settings: 
|
| 2 |
Select the tab SSO > Add SSO configuration, enter the Domain name and select Continue. 
|
| 3 |
Contact the person in your organization with access to the hostmaster@your.domain.name email inbox to retrieve the verification key that proves that you own the domain. 
|
| 4 |
Enter the verification key in Viedoc and select Verify. 
|
| 5 |
Make a note of the Redirect URL and the Entity ID. 
|
| 6 |
In a separate tab, log in to the Microsoft Azure portal and go to Azure Active Directory. Select Enterprise Applications > New application and Non-gallery application. 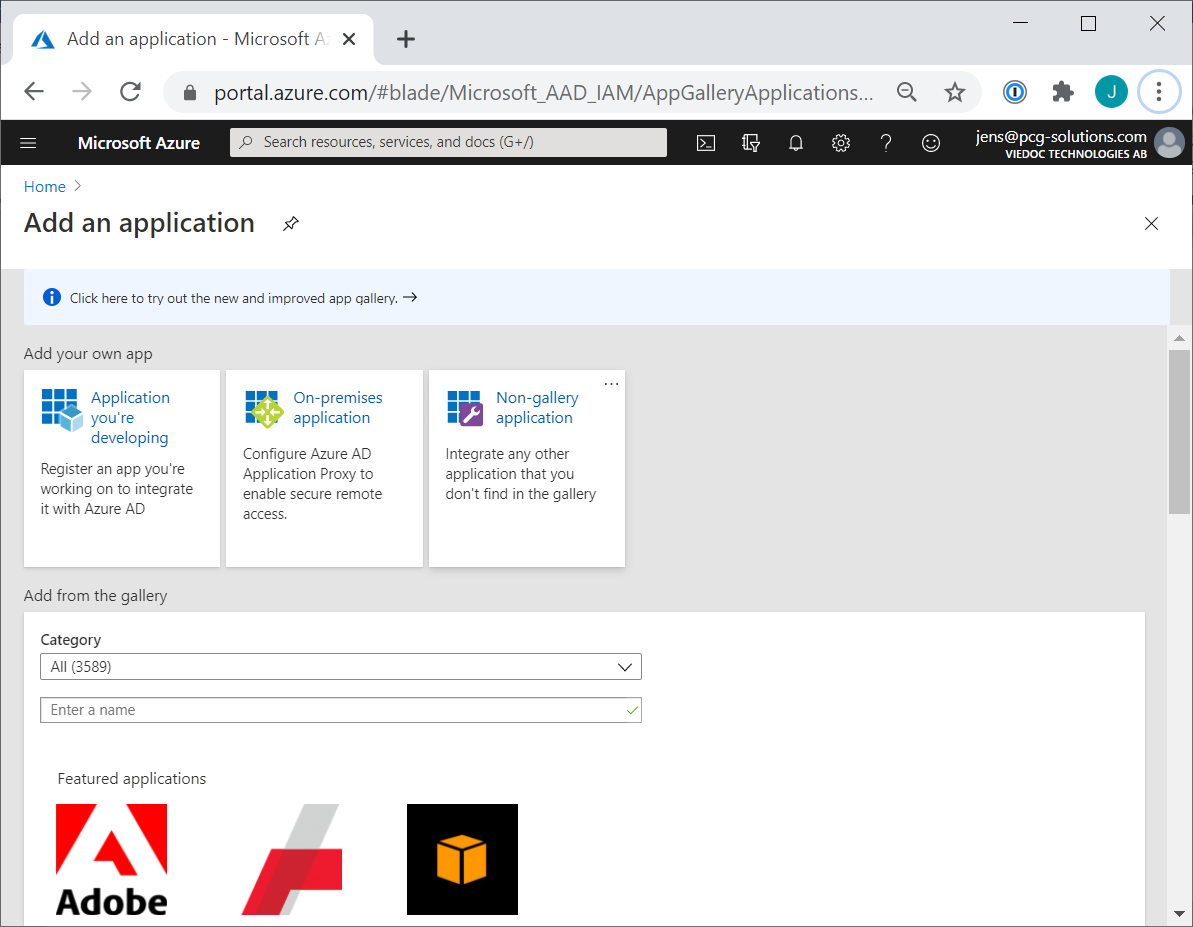
|
| 7 |
Enter an appropriate Name describing the Viedoc instance, for example “Viedoc Training SSO”. Select Add. 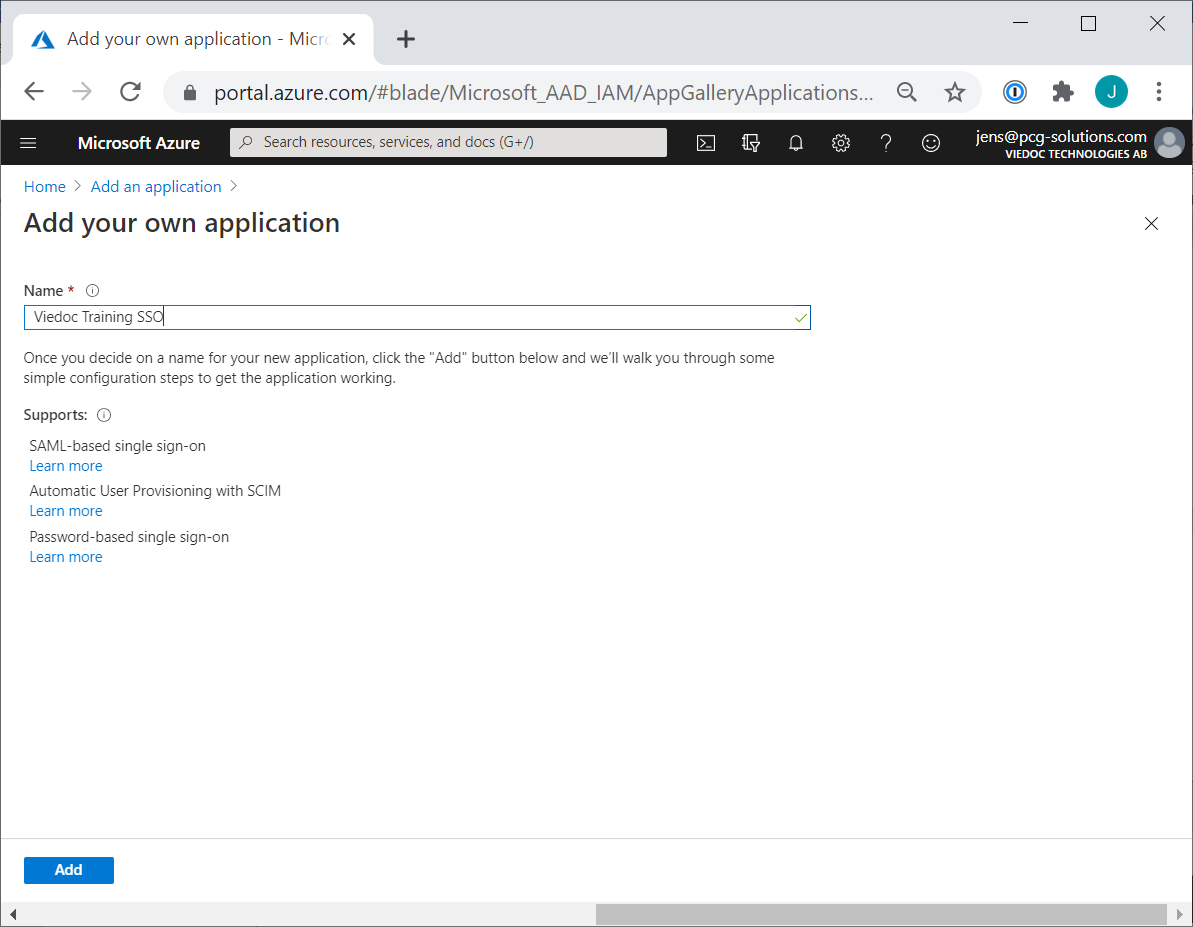
|
| 8 |
Select Single Sign-On > SAML. 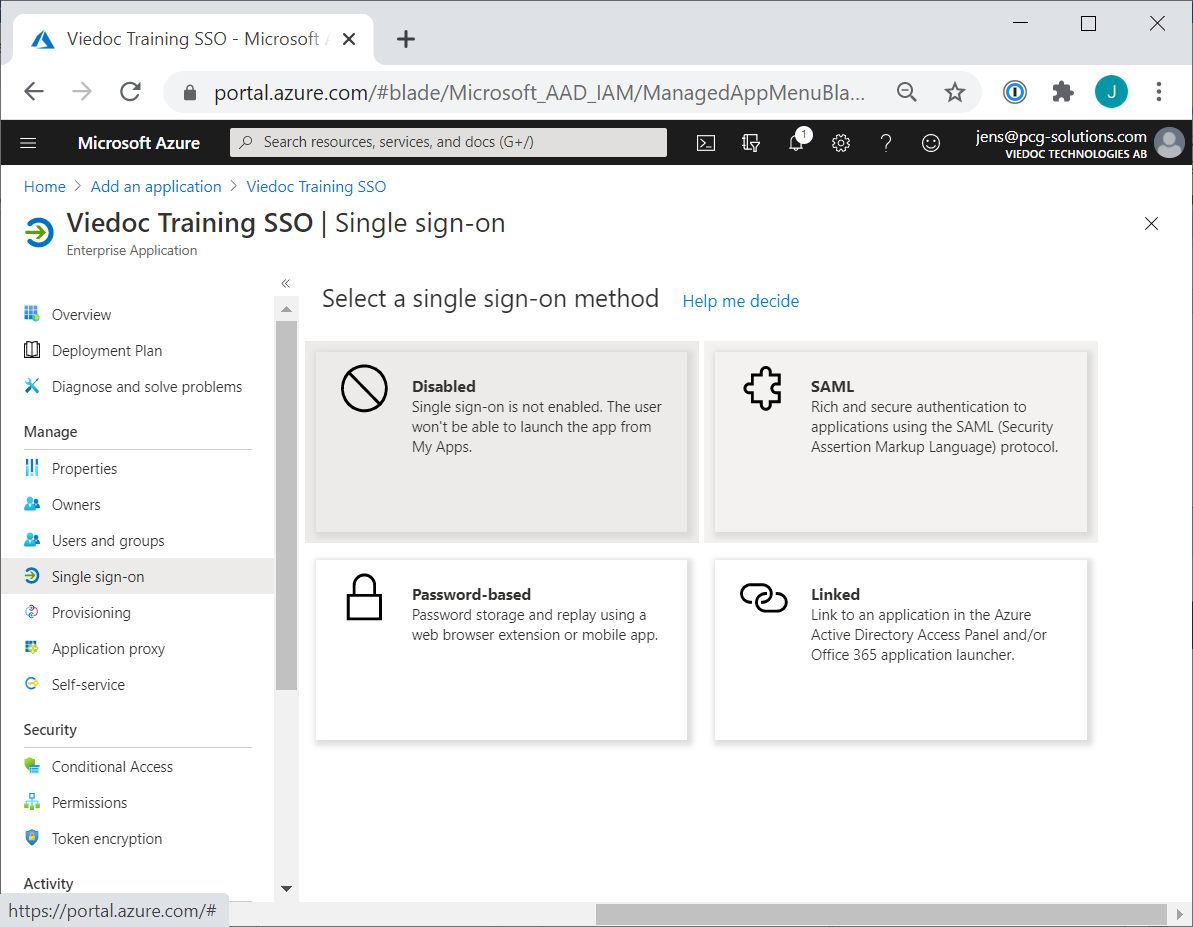
|
| 9 |
Select Edit the Basic SAML Configuration. From the Viedoc tab, copy and paste:
select Save and close the pop-up. 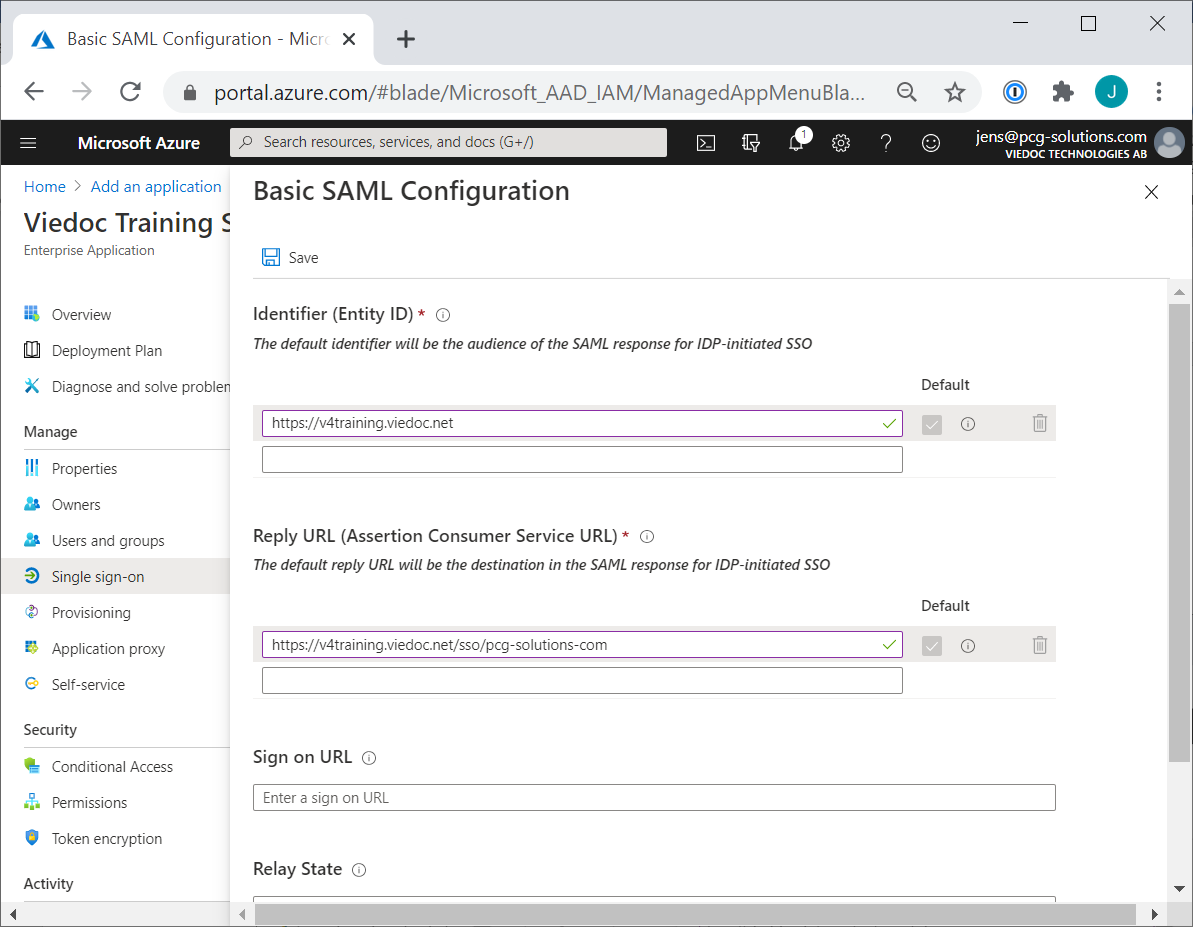
|
| 10 |
Select to Edit the User Attributes & Claims. 
|
| 11 |
Map the Unique User Identifier (Name ID) to the attribute that best matches the email address that users authenticate with in Viedoc, typically [user.userprincipalname] or [user.mail]. 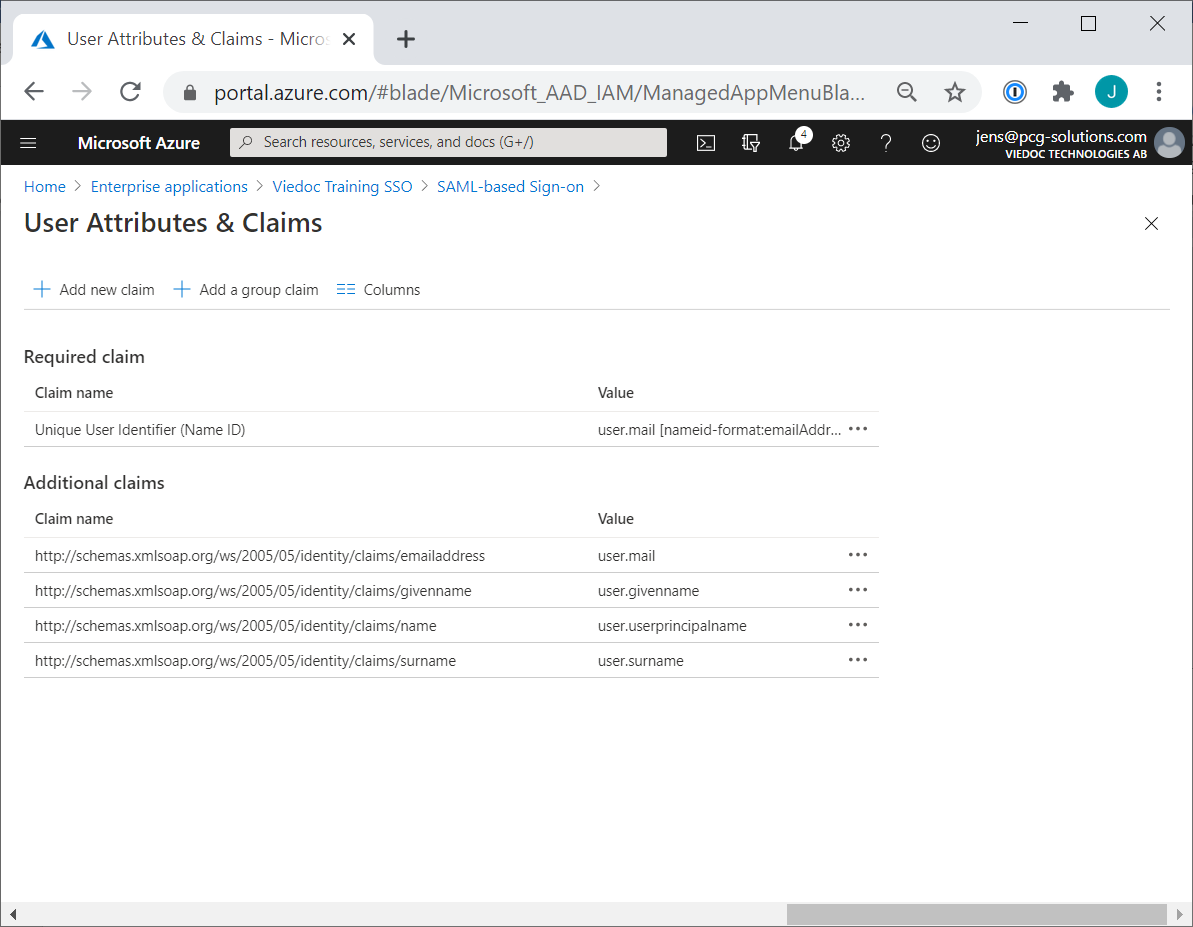
|
| 12 |
From the Azure AD window:
Select Save. 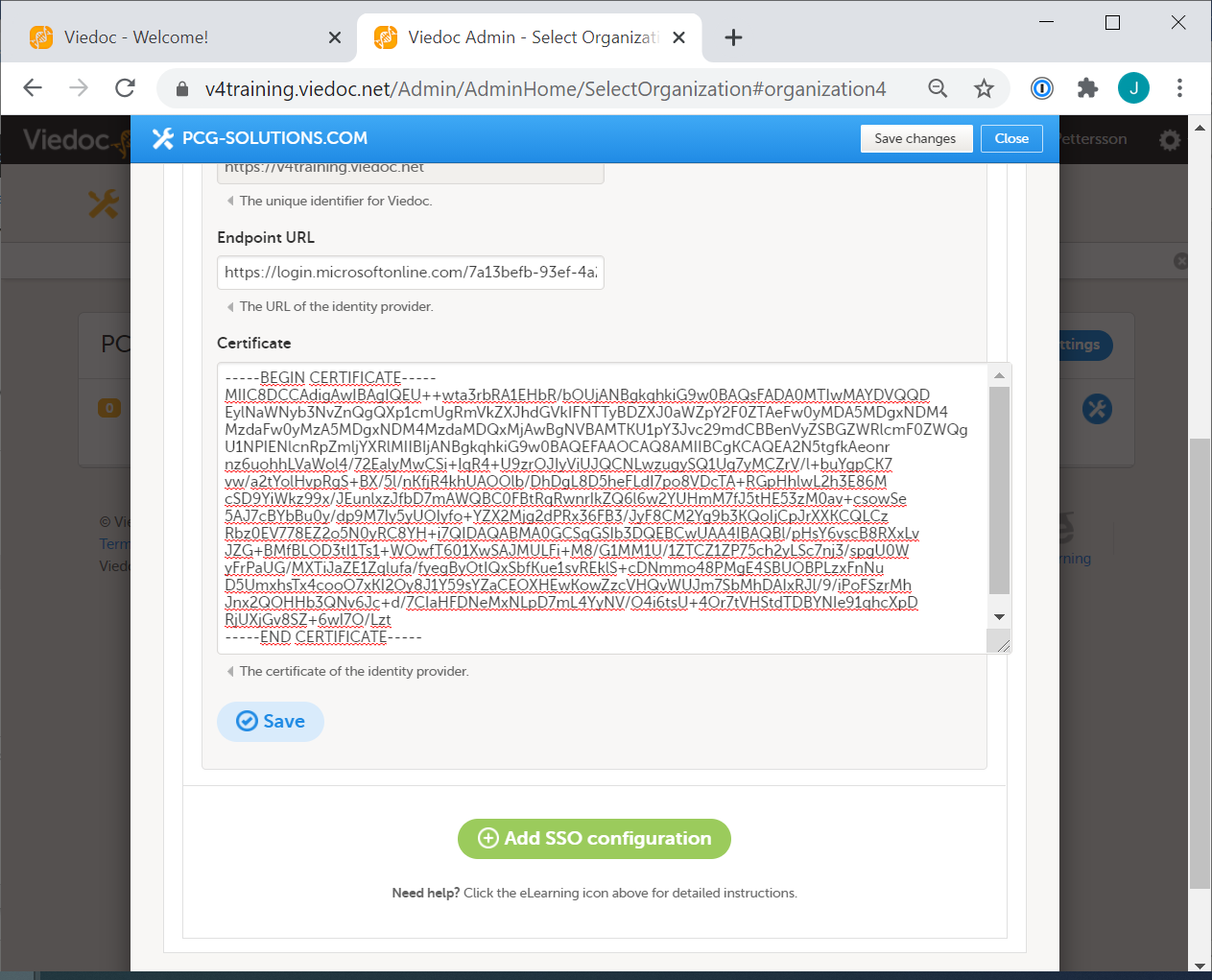
|
| 13 |
Download the Viedoc logo from the following URL https://www.viedoc.com/viedoc-msaad-sso-256x256.png and upload it to the Properties section in the Azure AD tab. 
|
| 14 |
Under Users and groups, add all users or security groups that shall be able to log in to Viedoc using SSO. 
|
| 15 |
Go back to the Viedoc tab and select Validate. Note! You might be promted to enter your email address and password in order to authenticate with your IdP if not already logged in. Upon successful authentication you will automatically be redirected to the domain verification page. 
|
| 16 |
Verify that the domain is validated and then close the tab. 
|
| 17 |
Select Next. 
|
| 18 |
The SSO configuration is now completed. When all users are informed about the new login URL—with the configured domain as their login name (the primary email address is used for authentication in both the IdP and in Viedoc)—select Activate > Yes. 
|
| 19 | Log out and log in using the new login URL. You will now be authenticated and redirected to the newly configured external IdP. |
SSO preparation checklist for Hostmasters
Before you activate Single Sign-On (SSO), make sure your organization is fully prepared by completing the checklist below.
-
Verify user email alignment
Ensure that the email addresses used for the Viedoc accounts match what is on file in the external IdP (for example, Google Workspace or Azure Active Directory). If the emails do not match, affected users will not be able to log in. -
Confirm domain ownership within your company
Check whether you are the only organization in Viedoc that is using this specific email domain. There may be other groups in your company that are using the same email domain and Viedoc. You will be activating SSO for them as well, so make sure they are also prepared (see item 1 above). -
Communicate the activation date and new login URL
Inform all users when SSO will be activated, and provide them with the new login URL. Users will be redirected to the new URL if they use the old one, but communicating the change in advance helps avoid confusion. -
Plan for certificate renewal
The SSO certificate expires after one year. Set an external reminder to renew the certificate before it expires. An expired SSO certificate will prevent users from logging in.
